An iconographic and text archive related to communication, technology and art.
☛ Arbor Networks Security: “Egypt Loses the Internet” by Craig Labovitz, January 28th, 2011
Labovitz, chief scientist for Arbor Networks –a “provider of network security and monitoring solutions for global networks”– explains:
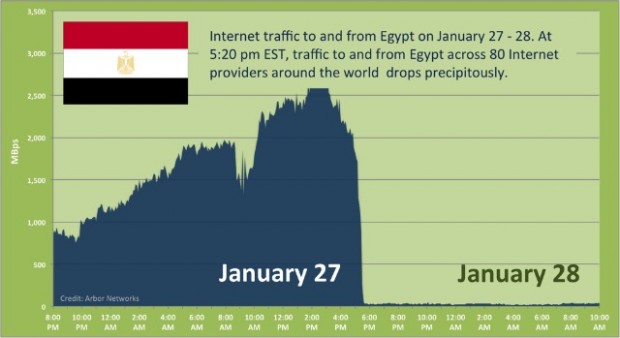
Following a week of growing protests and periodic telecommunication disruption, Egypt suddenly lost all Internet connectivity at approximately 5:20pm EST Thursday.
The [above] graph shows traffic to and from Egypt based on ATLAS data from 80 providers around the world.
Between 3 and 5pm EST, Egyptian traffic rapidly climbed to several Gigabits. At 5:20pm, the all Egyptian transit providers abruptly withdrew the major of Egypt’s several thousand BGP routes and traffic dropped to a handful of megabits per second.
At present, the cause of the outage is unknown though many press reports have drawn parallels to the Internet outages following Iranian political protests during the summer of 2009. Further, the simultaneous failure of Internet across multiple different Egyptian ISPs and diverse physical paths (i.e. satellite, fiber optic, etc) suggests this was a coordinated event rather than a natural failure. Typically, telecommunication companies operate under strict regulatory control in many countries around the world.
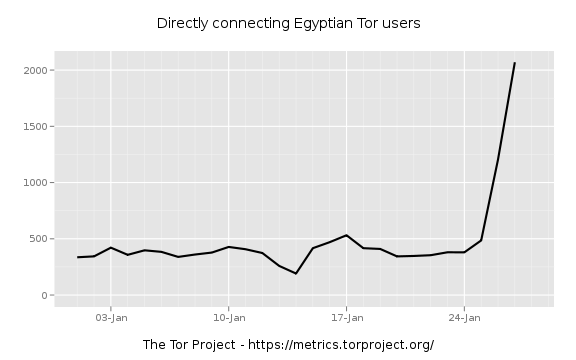
Meanwhile, the number of Egyptians using Tor to connect to the Internet “has skyrocketed” according to Jacob Applebaum, a core member of the Tor Project:
Tor is a system allowing a certain degreee of anonymity while surfing the Internet:
Tor is a network of virtual tunnels that allows people and groups to improve their privacy and security on the Internet. It also enables software developers to create new communication tools with built-in privacy features. Tor provides the foundation for a range of applications that allow organizations and individuals to share information over public networks without compromising their privacy. (About Tor, see also the Wikipedia article. To learn more about Jacob Applebaum, see this August 2010 article from the Rolling Stone magazine: “The Most Dangerous Man in Cyberspace”)
Tor software and installation instructions can be found here.
See also:
- The Boston Globe: “Foreign activists stay covered online. Mass. group’s software helps avoid censorship” by Farah Stockman, January 30, 2011.
- CBC News: “Busting Egypt’s web blackout. Savvy Egyptians using dial-up connections, unused ports to stay connected” by Peja Bulatovic, January 28, 2011.
Yet, one must be careful when considering Tor’s capabilities. Jacob Applebaum writes with caution:
There is a serious trade off to be made by users in hostile network environments with major political instability: Tor usage is possibly detectable with a skilled adversary. Connections made with questionable “privacy” or “security” proxy services are certainly easier than detecting Tor because of their static nature. The same is true of VPN services: all of these things are probably detectable with the right understanding and the proper equipment. It goes without saying that entirely unprotected connections to known unfavorable sites or services is detectable and well within the reach of the Egyptian network operators. (The Tor Blog)
In a document allegedly produced and distributed by Egyptian activists, there are specific directives pertaining to the use of popular social network tools:
“We ask you not to use Twitter of Facebook or other website because they are all monitored by the ministry of the interior”
This “Egyptian activist’s action plan” was obtain by Alexis Madrigal (The Atlantic) who, along with the help of others, translated excerpts of it and published them on his blog: “Egyptian Activists’ Action Plan: Translated”, January 27, 2011)
Internet is a powerful tool, granted. However, it would be a mistake to think of it as being intrinsically good, or being essentially a “revolution tool”. It’s a tool that can be used both ways, by uprising civilianss and oppressive regimes just as well. It should be used with caution (like any other tool).
For more on this particular problem see:
- The New Yorker: “Small Change. Why the revolution will not be tweeted” by Malcolm Gladwell, October 4th, 2010
- The Economist has a review of the newly published book The Net Delusion: The Dark Side of Internet Freedom by Evgeny Morozov. Here’s an excerpt of the review:
So what does Mr Morozov propose instead of the current approach? He calls for “cyber-realism” to replace “cyber-utopianism”, making it clear that he believes that technology can indeed be used to promote democracy, provided it is done in the right way. But he presents little in the way of specific prescriptions, other than to stress the importance of considering the social and political context in which technology is deployed, rather than focusing on the characteristics of the technology itself, as internet gurus tend to.
- By Philippe Theophanidis
- on
- ― Published in Communication, Technology
- Tagged: activism, critic, crowd, Egypt, Facebook, Internet, media, realism, révolution, Tor, Twitter, utopia